The $8.1M Gamble: An In-Depth Analysis of BigONE's Post-Hack Bounty and the Evolving Landscape of Crypto Recovery
Researched By - Ashikur Rahaman
The $8.1M Gamble: An In-Depth Analysis of BigONE's Post-Hack Bounty and the Evolving Landscape of Crypto Recovery
Executive Summary
This report provides an exhaustive analysis of the July 2025 security breach at the BigONE cryptocurrency exchange and its subsequent, unconventional response: the launch of an $8.1 million hack bounty program. The incident, which resulted in the loss of approximately $27 million in digital assets, marks a significant inflection point in the cat-and-mouse game between crypto platforms and sophisticated threat actors. The attack vector was not a common private key compromise but a highly complex supply chain attack, wherein attackers manipulated the exchange's internal business logic to authorize withdrawals. This methodological shift from cryptographic to operational security highlights a critical and often overlooked vulnerability in the infrastructure of centralized exchanges.
In response, BigONE initiated a multi-faceted crisis management strategy, pledging full user compensation and launching a high-stakes bounty program on the HackenProof platform. This program, offering up to 30% of recovered funds, is analyzed herein not merely as a fund recovery tool but as a complex strategic maneuver. It functions as a form of coercive negotiation, designed to increase the risk and difficulty of laundering the stolen assets, thereby making the bounty offer a more attractive path of least resistance for the perpetrators. The public disclosure of attacker Indicators of Compromise (IOCs) as part of the bounty is a key element of this strategy, weaponizing the transparency of the blockchain to crowdsource the investigation and apply pressure.
However, the incident and BigONE's response are complicated by pre-existing allegations from on-chain investigators regarding the exchange's role in processing illicit funds. This reputational context has muted community sympathy and reframes the bounty program as a dual-purpose initiative: one aimed at both financial recovery and reputational laundering.
By placing the BigONE hack in context with other seminal exchange breaches at KuCoin and Binance, this report benchmarks the evolution of incident response strategies. It further examines the growing, ethically fraught trend of post-hack bounties, weighing their pragmatic effectiveness against the risk of legitimizing criminal activity. The analysis concludes that the BigONE incident serves as a crucial case study, offering critical lessons for exchanges on the necessity of securing the entire software development lifecycle, and providing a framework for stakeholders to evaluate exchange trustworthiness in an increasingly complex threat environment.
Section 1: Anatomy of a Next-Generation Heist: The $27 Million BigONE Breach
The security incident at BigONE in mid-July 2025 was not a conventional crypto heist. It represented a sophisticated, next-generation attack that bypassed many of the security measures typically considered the bedrock of exchange safety. A detailed examination of the attack vector, the subsequent on-chain forensic trail, and the exchange's initial crisis communications provides a foundational understanding of the event that precipitated the unprecedented bounty program.
1.1 The Attack Vector: Deconstructing the Sophisticated Supply Chain Compromise
On approximately July 15-16, 2025, the Seychelles-based cryptocurrency exchange BigONE suffered a security breach resulting in the unauthorized withdrawal of digital assets valued at around $27 million from one of its hot wallets.1 Subsequent investigations by blockchain security firms SlowMist and Cyvers quickly identified the intrusion not as a simple theft of credentials but as a far more intricate "supply chain attack".3 This classification is critical, as it signifies a fundamental shift in attack methodology away from direct assaults on cryptographic key security.
The attack's execution path, as detailed in BigONE's own post-mortem and analysis from security partners, began with a classic but highly effective entry point: social engineering. The attackers successfully targeted and compromised the development device of a key BigONE developer, which served as the foothold to gain unauthorized access and crucial permissions within the exchange's network.6
From this compromised position, the attackers executed the core of the supply chain attack. They injected tampered code into the exchange's production environment through its version deployment service providers, likely compromising the Continuous Integration and Continuous Deployment (CI/CD) pipeline.4 This is a tactic well-documented in major traditional cybersecurity events, such as the SolarWinds breach, but is a less common vector for high-profile crypto exchange exploits.7
The genius of this attack lies in what the malicious code was designed to do. Instead of attempting to exfiltrate the hot wallet's private keys—which BigONE has consistently stated remained secure—the code altered the core operational logic of the exchange's internal accounting and risk control servers.3 By modifying this business logic, the attackers effectively granted themselves the ability to bypass standard withdrawal limits and security checks, enabling them to execute a series of large, unauthorized transfers. In essence, the attackers did not need to break into the vault; they reprogrammed the vault's own systems to open the door for them.10
This method represents a significant evolution in the threat landscape for centralized exchanges. It demonstrates that perfect cryptographic security and robust wallet architecture can be rendered moot if the operational software and development pipelines that interact with those wallets are insecure. This "soft underbelly" approach, targeting the trust inherent in the software development lifecycle, has profound implications for how exchanges must now view their security posture, expanding the critical attack surface far beyond the wallet itself.4
1.2 On-Chain Forensics: Tracing the Stolen Assets Across Multiple Blockchains
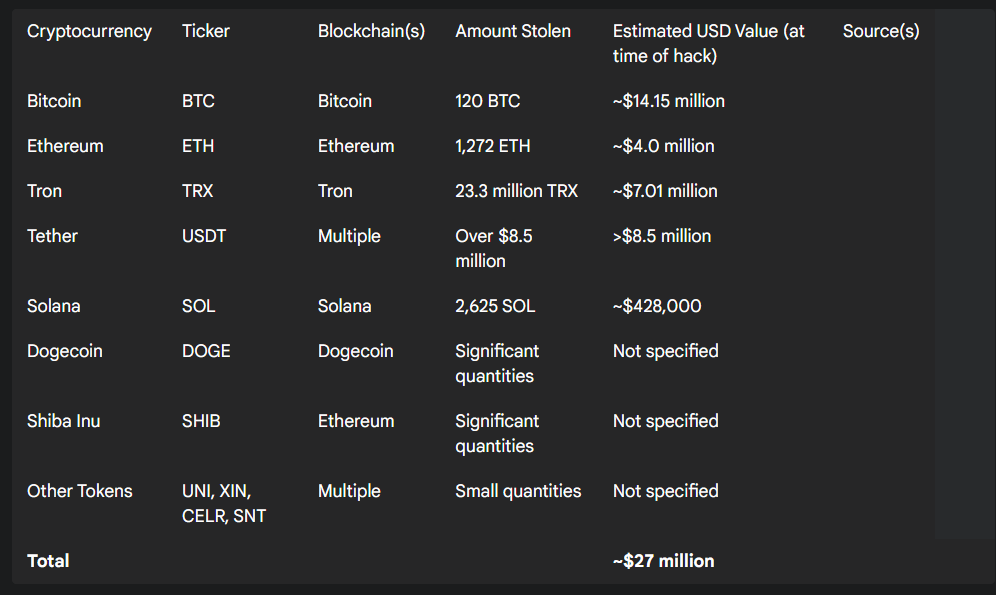
The attackers leveraged their control over the exchange's withdrawal logic to drain a diverse portfolio of assets across at least four major public blockchains: Bitcoin, Ethereum, Solana, and Tron.3 The multi-chain nature of the theft complicated initial tracing efforts and demonstrated the attackers' proficiency in operating across different crypto ecosystems.
On-chain analysis from firms like Lookonchain, CertiK, and Cyvers, combined with BigONE's own disclosures, painted a detailed picture of the stolen funds.1 The heist included high-value, liquid assets, indicating the attackers prioritized ease of laundering and conversion over targeting more obscure tokens. The attackers immediately began a sophisticated laundering process, routing the stolen assets through a web of decentralized exchanges (DEXes) and cross-chain bridges. This strategy is designed to obfuscate the origin of the funds by swapping them for other tokens—primarily more liquid ones like ETH, SOL, and BNB—and moving them between blockchains to break the forensic trail.4 As part of its subsequent bounty program, BigONE took the step of publicly disclosing the primary wallet addresses on each blockchain where the stolen funds were consolidated, a strategic move aimed at empowering white hat researchers and increasing pressure on the attackers.6
A consolidated view of the stolen assets is detailed in the table below.
1.3 Crisis Management Under Fire: BigONE's Initial Response and Communications
BigONE's initial public handling of the crisis drew scrutiny from industry observers. The first communication related to the incident was a vague "system maintenance" or "system upgrade" announcement.3 This was posted hours before the exchange formally acknowledged the hack, a tactic often viewed critically as either an attempt to control the narrative before releasing bad news or a sign of internal chaos where the communications team is not in sync with the security team's findings.
Several hours later, BigONE issued a formal "Security Incident" announcement, confirming the "unauthorized access to our hot wallet".3 From that point, the exchange enacted a series of standard, yet critical, crisis response measures. It immediately suspended all deposit and withdrawal functions to contain the breach and prevent further losses.2 In its communications, the exchange was quick to reassure its user base on two key points: that their personal data and the private keys to all wallets remained secure, and that the company would fully cover all user losses resulting from the incident.1 The promise that "user assets will not be affected in any material way" was a crucial message aimed at preventing a bank run and preserving customer trust.1
To make good on this pledge, BigONE announced the activation of its internal insurance and security reserve fund, which reportedly held a mix of BTC, ETH, USDT, SOL, and XIN tokens. For other affected assets where reserves were insufficient, the exchange stated it was actively securing external liquidity through borrowing mechanisms.2 Concurrently, BigONE partnered with cybersecurity firms SlowMist and Cyvers to assist with the investigation, trace the stolen funds, and analyze the attack vector.1
The exchange worked to restore functionality swiftly, bringing deposit and trading services back online around 10:30 UTC on July 16. However, withdrawals remained suspended pending further security reinforcements, a necessary precaution to ensure the vulnerability was fully patched before reopening all financial outflows.2
Section 2: The $8.1 Million Bounty: A Strategic Analysis
In the aftermath of the breach, BigONE's most significant and strategic move was the launch of a massive public bounty. This was not a standard bug bounty for finding new vulnerabilities, but a targeted, post-hack recovery program designed to reclaim the stolen $27 million. An analysis of the program's architecture, its underlying rationale, and its use of strategic intelligence disclosure reveals a sophisticated approach to crisis management that is uniquely tailored to the cryptocurrency ecosystem.
2.1 Program Architecture: A Detailed Examination of the HackenProof Recovery Bounty
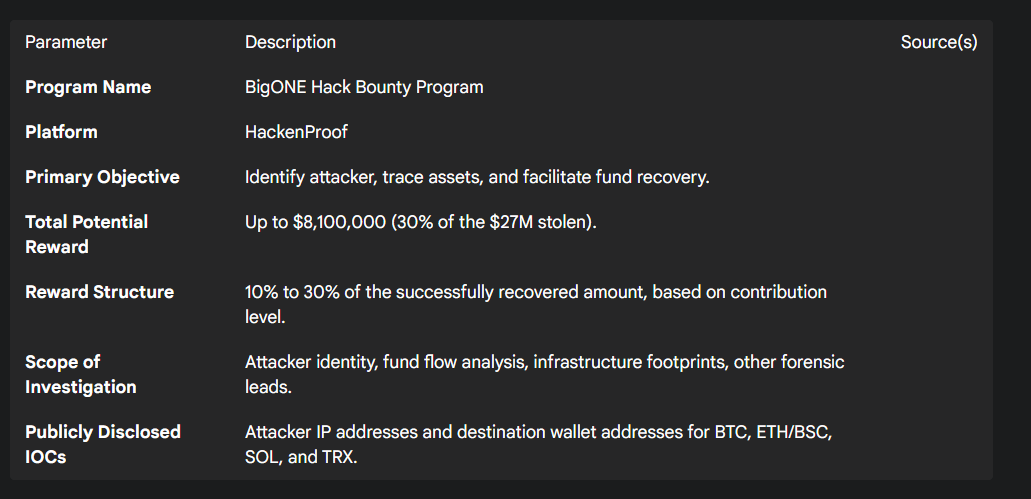
BigONE launched its "Hack Bounty Program" on HackenProof, a well-known platform for bug bounties, deliberately choosing a public and reputable venue for the initiative.6 This distinguished it from their ongoing, much smaller, standard bug bounty program and signaled the gravity of the effort.15 The program's stated objectives are explicit and threefold: to identify the individuals or group responsible for the attack, to trace the movement of the stolen assets, and, most importantly, to facilitate the recovery of the funds.6
The headline figure of the program is an eye-catching $8.1 million. However, this is not a guaranteed prize pool but a potential maximum payout, representing 30% of the total stolen amount.6 The reward structure is entirely performance-based and contingent on success. The terms state that a bounty of 10% to 30% of the
recovered amount will be awarded to those who provide verified and effective intelligence that leads directly to asset recovery. The percentage awarded depends on the significance of the contribution, creating a powerful incentive for high-impact results.6
To aid this crowdsourced investigation, BigONE defined a clear scope for white hat researchers, seeking specific categories of information:
Attacker Identity Clues: Any on-chain or off-chain data that could help deanonymize the attackers, such as linked wallet addresses, social media accounts, or activity on other centralized exchanges.
Fund Flow Analysis: Detailed on-chain tracking, including the identification of coin mixing services, cross-chain laundering techniques, and patterns in fund movements.
Infrastructure Footprints: Associated IP addresses, domains, hosting providers, or server infrastructure used in any phase of the attack.
Other Forensic Leads: Any additional evidence that could assist in the investigation.6
The key parameters of this unique bounty program are summarized in the table below.
2.2 The Rationale and Risks: A Calculated Move for Fund Recovery and Reputation Management
The decision to launch such a high-profile bounty program is a calculated one, driven by a blend of pragmatic financial incentives, public relations strategy, and coercive negotiation tactics.
The primary and most obvious rationale is fund recovery. In the world of decentralized finance, stolen assets can be moved and laundered through a global, pseudonymous network of DEXes, mixers, and cross-chain bridges with incredible speed. Traditional law enforcement channels are often too slow and jurisdictionally constrained to act effectively.16 Offering the attacker a significant percentage of the loot as a "no questions asked" bounty is frequently the most direct, and sometimes only, viable path to recovering a portion of the losses.18
The secondary rationale is reputation management. A major security breach inevitably erodes user trust. By launching an aggressive and transparent bounty program, BigONE projects an image of proactivity and strength. It shifts the public narrative from "BigONE was a victim of a hack" to "BigONE is actively fighting to recover funds and bring the perpetrators to justice," a crucial step in reassuring customers and the market that the exchange is a responsible custodian.11
A tertiary, more subtle rationale is coercive negotiation. The act of publicizing the bounty, along with the attacker's known wallet addresses and IOCs, significantly increases the operational risk for the attacker. The stolen funds become "hot," making them difficult to deposit on compliant exchanges or use in services that monitor blacklists. This pressure is designed to degrade the value and utility of the stolen assets to the attacker, thereby making the offer of 10-30% in "clean," risk-free bounty money a more appealing alternative to the difficult and dangerous process of laundering the full amount.19
However, this strategy is not without significant risks. The most prominent is the ethical hazard of legitimizing crime. Paying the perpetrator is functionally similar to paying a ransom, and it can be argued that this practice establishes a "market rate" for successful exploits, potentially encouraging future attacks by demonstrating a profitable exit strategy for criminals.18 Furthermore, the
success rate of such bounties is far from guaranteed. Analysis of past incidents shows that more than half of public bounty offers in the crypto space are ignored, particularly if the attacker is a sophisticated state-sponsored actor or is confident in their ability to launder the funds without being caught.18
2.3 Strategic Intelligence Disclosure: Analyzing the Release of Attacker IOCs and Wallet Addresses
A cornerstone of BigONE's bounty strategy was the public release of key Indicators of Compromise (IOCs). The bounty program announcement included a list of IP addresses used in the attack and the specific destination wallet addresses on the Bitcoin, Ethereum, Solana, and Tron blockchains where the stolen funds were initially consolidated.6
This disclosure of sensitive forensic data is a deliberate and multi-pronged tactic. First, it empowers the white hat community. By providing the raw data, BigONE effectively crowdsources the monumental task of on-chain tracing and analysis to a global community of security researchers, each bringing their own tools and expertise to bear on the problem.6
Second, it applies public pressure throughout the crypto ecosystem. With the attacker's addresses made public, other exchanges, custodians, and blockchain analytics firms can immediately flag them, making it significantly harder for the attacker to move or cash out the funds through any legitimate, compliant service.
Third, it serves as a tool for disruption and deterrence. Publicizing the attacker's operational infrastructure, such as their IP addresses, can help other potential targets identify and block similar threats, while also potentially disrupting the attacker's ability to use that same infrastructure for other activities.
This approach represents a sophisticated form of information warfare unique to the transparent nature of public blockchains. While in traditional cyber investigations such IOCs might be kept confidential to avoid tipping off the adversary, in the crypto world, leveraging public visibility can become a powerful tool to corner an attacker and manipulate their risk-reward calculation.
Section 3: Industry Context and Comparative Benchmarking
No exchange hack occurs in a vacuum. The BigONE incident and its response must be understood within the broader context of historical security breaches and the evolving playbook for post-hack recovery. By comparing BigONE's actions to those of other major exchanges like KuCoin and Binance, and by analyzing the burgeoning trend of post-hack bounties, a clearer picture emerges of industry best practices, strategic trade-offs, and the economic rationale for proactive security.
3.1 A Comparative Review of CEX Hack Responses: BigONE vs. KuCoin (2020) and Binance (2019 & 2022)
The responses of centralized exchanges (CEXs) to major security breaches have varied significantly, shaped by the nature of the attack, the assets stolen, and the leadership's philosophy on transparency and compensation. Comparing the BigONE incident to other seminal hacks provides valuable benchmarks.
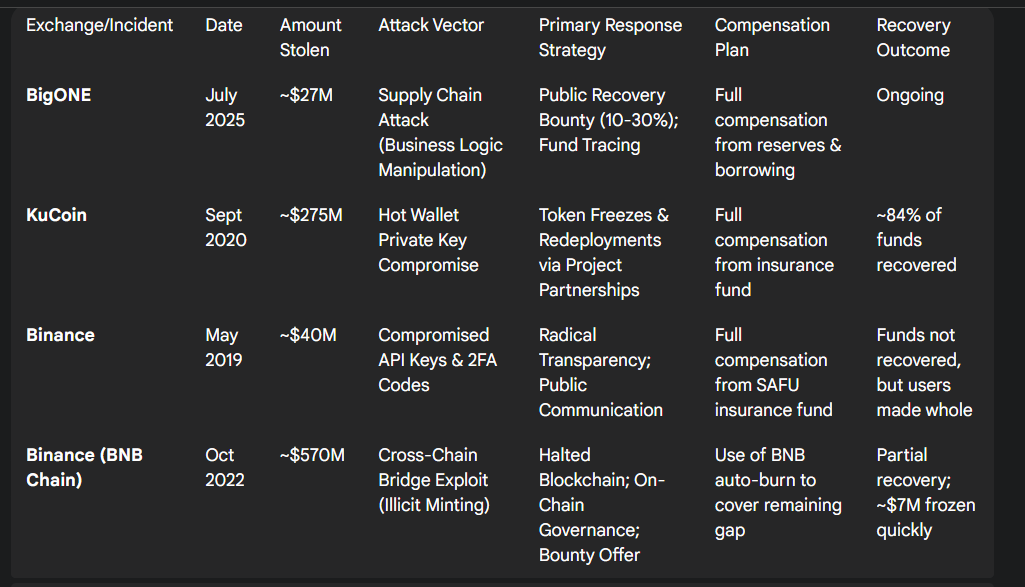
KuCoin (September 2020, ~$275M Hack): The attack on KuCoin involved the compromise of private keys to its hot wallets, with the North Korean Lazarus Group later identified as the perpetrator.3 The stolen assets were predominantly ERC-20 tokens. KuCoin's response was a masterclass in ecosystem collaboration. Rather than relying on a public bounty, the exchange worked directly with the teams behind the stolen tokens (like Tether and Orion Protocol) to freeze the assets or execute contract upgrades and redeployments. This action rendered a significant portion of the stolen tokens worthless to the hackers.23 Coupled with on-chain tracking and cooperation with law enforcement, this strategy led to the recovery of an astonishing 84% of the funds (over $204 million) within two months.23
Binance (May 2019, ~$40M Hack): In this incident, hackers used a combination of phishing, viruses, and other attack vectors to gain control of user API keys and 2FA codes, allowing them to steal 7,000 BTC in a single transaction.25 CEO Changpeng "CZ" Zhao's response set a new standard for crisis communications. He was radically transparent, providing constant updates via social media. He famously floated, and then quickly backtracked on, the controversial idea of attempting a Bitcoin network rollback to reverse the transaction. Crucially, Binance announced it would cover all user losses in full from its Secure Asset Fund for Users (SAFU), an emergency insurance fund financed by a portion of trading fees. This action preserved user trust, and the transparent response was widely praised, even as recovery of the stolen Bitcoin proved difficult.25
Binance (October 2022, ~$570M BNB Chain Hack): This was not a hack of the exchange itself, but an exploit of the BSC Token Hub, a cross-chain bridge. The attacker exploited a vulnerability that allowed them to mint 2 million new BNB tokens out of thin air, rather than stealing existing assets.27 The immediate response was to halt the entire BNB Chain to contain the damage. The recovery strategy involved on-chain governance votes to freeze hacked funds and a proposal to offer a bounty for the return of the remaining funds, alongside the establishment of a new bug bounty program to prevent future incidents.27
BigONE's 2025 response appears to be a hybrid of these precedents. Like Binance, it immediately pledged full compensation from a reserve fund and engaged in public communication (albeit after an initial delay). However, because the primary assets stolen were BTC and native chain tokens, it could not rely on the token-freezing strategy that was so effective for KuCoin. This makes its reliance on a public recovery bounty, similar to the one proposed after the BNB Chain exploit, a more central and critical component of its strategy.
3.2 The Rise of Post-Hack Bounties: Evaluating Effectiveness and Ethical Dilemmas
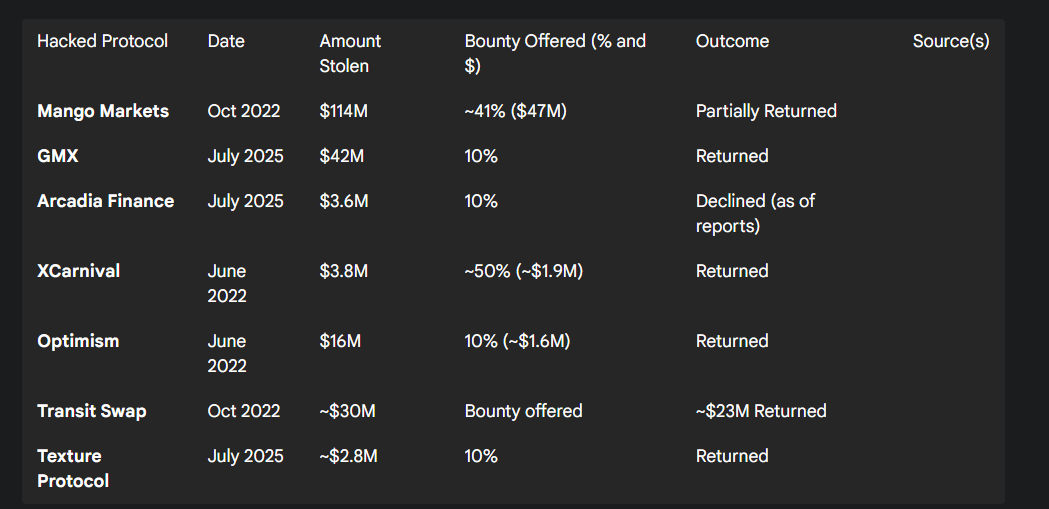
The strategy of offering a public bounty to an attacker for the return of stolen funds has become an increasingly common, if controversial, tool in the crypto incident response playbook. TRM Labs identified at least 20 such incidents in 2022 alone, with these programs facilitating the return of over $160 million.18
These "white hat" deals, as they are sometimes called, have seen notable successes. In the wake of a $114 million exploit, Mango Markets successfully negotiated the return of a portion of its funds by offering the attacker a $47 million bounty.18 Similarly, protocols like GMX, Texture Protocol, and Transit Swap have all recovered significant percentages of stolen funds by offering the hacker a 10% cut as a bounty.29 The rationale for the hacker to accept is compelling: they receive a large sum of "clean" money without the risk, effort, and cost associated with laundering the full, tainted amount through complex mixing services.19
However, the strategy is far from foolproof. Over half of such public offers are declined or simply ignored.18 This is especially true when the perpetrators are state-sponsored groups, such as North Korea's Lazarus Group, who are not motivated by personal wealth and are less concerned with the consequences of being identified.18 Attackers who are confident in their operational security and laundering capabilities may also choose to reject the offer and attempt to keep the entire haul.
This practice exists in a deep ethical gray zone. Critics argue that calling these payments "bounties" is a euphemism for paying a ransom. They contend that it legitimizes criminal activity, rewards bad actors, and creates a perverse incentive structure where hacking becomes a viable business model with a negotiated exit.19 Proponents, on the other hand, view it as a pragmatic last resort. In an ecosystem where assets are bearer instruments and can vanish across borders in minutes, it is often the only realistic chance a victimized project has to recover any funds and make its users whole.30
3.3 Proactive vs. Reactive Security: The Economic Case for Pre-Emptive Bug Bounties
While post-hack recovery bounties are a necessary reactive tool, their increasing prevalence underscores a more fundamental truth: proactive security is exponentially more valuable and cost-effective. The most effective way to deal with a hack is to prevent it from happening in the first place. This is the economic and strategic case for robust, pre-emptive bug bounty programs.32
These programs incentivize ethical hackers and security researchers to find and responsibly disclose vulnerabilities before they can be exploited by malicious actors. The economic calculus is stark. Aurora, an Ethereum scaling solution, famously paid a $6 million bug bounty to a researcher who discovered a critical flaw that could have led to a $200 million loss.18 Paying $6 million to prevent a $200 million catastrophe is an unequivocally sound business decision. In contrast, BigONE's own standard bug bounty program offers a maximum reward of just $1,500 for critical vulnerabilities—a figure completely dwarfed by the $27 million loss and subsequent multi-million dollar recovery effort from this single incident.15
Beyond direct cost savings, proactive bug bounties offer immense strategic advantages. They leverage the collective intelligence of the global security community, providing a continuous and adaptive form of security testing that is impossible for an internal team or a one-time audit to replicate.21 A well-funded, responsive, and transparent bug bounty program also serves as a powerful signal to the market. It demonstrates a project's deep commitment to security, which in turn builds the user trust and brand reputation that are the most valuable assets for any financial institution.32
Section 4: Reputational Fallout and Community Sentiment
The technical details of the BigONE hack and the strategic design of its bounty program tell only part of the story. The incident's impact has been significantly shaped by the non-technical context of the exchange's reputation and the broader community's reaction. Allegations of past misconduct have complicated the narrative of victimhood, while the bounty itself has been met with a mix of interest and skepticism from the white hat community.
4.1 The ZachXBT Allegations: Illicit Fund Flows and the Complication of Victimhood
In the immediate aftermath of the hack, a significant portion of the crypto community's reaction was shaped by commentary from the prominent on-chain investigator, ZachXBT. Rather than offering sympathy, ZachXBT publicly stated he did "not feel bad for the team," alleging that the BigONE exchange has a history of processing large volumes of illicit funds.5 Specifically, he claimed the exchange was a nexus for proceeds from "pig butchering," romance, and investment scams, citing one deposit address that allegedly processed at least $60 million in scam-related funds over a seven-month period.36
These allegations, coming from a widely respected figure in the on-chain analysis community, fundamentally altered the public perception of the incident. They painted a picture of an exchange with potentially lax Anti-Money Laundering (AML) and Know Your Customer (KYC) controls, despite its stated policies of adhering to such standards.10 This transformed the narrative from a straightforward case of a legitimate business being victimized by criminals into a more complex and morally ambiguous situation.
For some observers and community members, the hack was viewed through a lens of karmic justice or as a "natural cleanse" of an ecosystem player perceived as enabling other forms of financial crime.10 This reputational baggage is not merely a public relations problem; it has tangible consequences. It erodes the goodwill and community support that can be vital during a crisis. An exchange seen as a "good actor" might rally the entire ecosystem to its aid, as seen with projects assisting KuCoin. An exchange with a tarnished reputation may find itself isolated, its calls for help and its recovery efforts undermined by a lack of trust. This context forces BigONE's bounty program to serve a dual purpose: it is not only an attempt to recover stolen funds but also a public performance of good corporate citizenship, aimed at repairing a damaged reputation.
4.2 The White Hat Perspective: Assessing the Bounty's Attractiveness and Feasibility
From the perspective of the ethical hacking and bug bounty community, BigONE's recovery program is a subject of intense interest, evaluated on its potential rewards and the practical feasibility of success.
The sheer size of the potential payout—up to $8.1 million—is exceptionally attractive and is certain to draw the attention of top-tier security researchers globally.14 This figure dwarfs the rewards offered by the vast majority of standard bug bounty programs, which typically pay in the thousands or, for the most critical findings at the largest companies, hundreds of thousands of dollars.15 The potential for a life-changing payout is a powerful motivator.
However, this attractiveness is tempered by significant feasibility challenges. First and foremost, attribution is exceptionally difficult. Unmasking the real-world identity of a sophisticated, nation-state-level or highly disciplined criminal hacking group is a monumental task, even with a public blockchain ledger. Attackers use a variety of techniques, from VPNs and compromised servers to cryptocurrency mixers and chain-hopping, to obscure their tracks.
Second, the program's structure creates intense competition and a high risk of uncompensated work. Many researchers will be pursuing the same leads simultaneously. According to the program's terms, only the first person or group to provide intelligence that directly leads to recovery will be rewarded.6 This means a researcher could invest hundreds of hours into the investigation, uncover significant findings, but receive no compensation if another party is slightly faster or if law enforcement is ultimately unable to seize the funds based on the intelligence provided.
Finally, the trustworthiness of the program itself is a key consideration for researchers. The bug bounty community is rife with stories of programs that are slow to respond, change the scope of their rules retroactively, or unfairly downplay the severity of a finding to avoid a large payout.40 BigONE's handling of this high-profile bounty—its responsiveness, fairness in evaluation, and timeliness of payment if successful—will be intensely scrutinized and will have a lasting impact on its reputation within the security research community.
Section 5: Strategic Implications and Recommendations
The BigONE security breach and its aftermath offer a series of critical lessons and strategic implications for the entire cryptocurrency industry. Synthesizing the technical, financial, and reputational dimensions of this incident provides a clear framework for fortifying exchange security, refining recovery strategies, and empowering stakeholders to make more informed decisions.
5.1 Fortifying the Core: Critical Security Lessons for Centralized Exchanges Beyond the Hot Wallet
The nature of the BigONE attack underscores that the security perimeter of a modern exchange extends far beyond its wallets. The following lessons are paramount for all centralized platforms:
Lesson 1: The Software Development Lifecycle (SDLC) is a Critical Attack Surface. The BigONE hack proves that an exchange's greatest vulnerability may not be its cryptography but its code deployment process. Exchanges must elevate the security of their CI/CD pipelines, third-party code dependencies, and developer endpoint management to the same level of criticality as wallet security. This includes strict access controls, mandatory code reviews for security implications, and integrity checks to prevent the deployment of tampered code.4
Lesson 2: Defense-in-Depth is Non-Negotiable. A single point of failure—in this case, a compromised developer and deployment pipeline—led to a catastrophic loss. This highlights the necessity of multi-layered security controls. Essential measures include implementing automated pre-transaction validation rules that flag abnormal withdrawal sizes or frequencies, enforcing strict network segmentation between development and production environments, and having automated incident response playbooks that can instantly halt withdrawals or move assets to cold storage when anomalies are detected.4
Lesson 3: The Human Factor Remains a Primary Vector. Technology and processes are only as strong as the people who manage them. The initial intrusion was achieved through social engineering targeting a developer.6 This reinforces the absolute necessity of continuous and rigorous employee training on phishing and other social engineering tactics, conducting thorough background checks for personnel in sensitive roles, and enforcing the principle of least privilege for all system access.42
5.2 The Future of Hack Recovery: The Interplay of Bounties, Insurance, and Law Enforcement
The response to the BigONE hack illustrates that crypto asset recovery is evolving into a complex, multi-pronged discipline. No single solution is a panacea; instead, a combination of strategies will define the future of recovery efforts.
Bounties: Post-hack bounties will persist as a pragmatic, if ethically controversial, tool. They offer a direct and rapid channel for negotiation with attackers, which is often the only viable path to partial recovery when funds are being actively laundered.18 Over time, a "market rate" for these bounties may continue to normalize around the 10-15% mark, establishing an informal industry standard.
Insurance: Self-funded insurance pools like Binance's SAFU and BigONE's own reserves will become an essential component of user trust and a key competitive differentiator. Exchanges that can credibly demonstrate they have the reserves to make users whole after a hack will have a significant advantage. Consequently, third-party cyber insurers will likely intensify their underwriting scrutiny, demanding proof of robust SDLC security and defense-in-depth controls before issuing policies.7
Law Enforcement & Forensics: While often slow to act, the capabilities of law enforcement are steadily improving. The growing sophistication of on-chain tracing tools from firms like Chainalysis and TRM Labs, combined with increasing international cooperation among agencies, means that the freezing and seizure of stolen assets is becoming more feasible, though it remains a significant challenge.17
5.3 A Framework for Due Diligence: Evaluating Exchange Security and Trustworthiness
For users, investors, and regulators, the BigONE incident provides a clearer framework for conducting due diligence on cryptocurrency exchanges. The evaluation must go beyond superficial metrics.
Look Beyond Trading Volume: Raw trading volume is an unreliable indicator of an exchange's quality, as it can be artificially inflated through wash trading—a practice BigONE has been accused of in the past.45 More holistic metrics like CoinGecko's Trust Score, which incorporates verified liquidity, scale of operations, and a cybersecurity score, offer a much more reliable assessment of an exchange's legitimacy.3
Key Indicators of a Secure and Trustworthy Exchange:
Proactive Security Posture: The existence of a public, well-funded, and responsive pre-emptive bug bounty program is a strong positive signal of a commitment to security.32
Financial Transparency: Regular, audited Proof of Reserves and clear public statements about the size and composition of insurance funds are critical for building trust.46
Third-Party Validation: Adherence to internationally recognized security certifications, such as SOC 2 Type II or ISO 27001, provides independent validation of an exchange's security controls.48
Compliance and Reputation: A clean public record, free from credible allegations of facilitating illicit fund flows, and evidence of strong, verifiable KYC/AML procedures are fundamental to establishing an exchange as a responsible actor in the financial ecosystem.
Ultimately, the BigONE hack serves as a stark reminder that in the digital asset space, security is not merely a feature; it is the fundamental product. Trust is not a given but is earned through relentless vigilance, radical transparency in times of crisis, and a demonstrable, holistic commitment to protecting user assets at every level of the organization.
Works cited
Crypto heist pilfers $27M from BigONE - SC Media, accessed July 19, 2025, https://www.scworld.com/brief/crypto-heist-pilfers-27m-from-bigone
This Week in Crypto Hacks: BigONE Suffers $27M Hot Wallet Hack, Vows Full User Compensation | CCN.com, accessed July 19, 2025, https://www.ccn.com/news/crypto/this-week-crypto-hacks-bigone-arcadia-finance/
BigOne exchange lost $27 million due to attack - Mitrade, accessed July 19, 2025, https://www.mitrade.com/insights/news/live-news/article-3-962394-20250716
Crypto exchange BigONE loses $27M in third-party attack - Cointelegraph, accessed July 19, 2025, https://cointelegraph.com/news/bigone-exchange-27m-hot-wallet-hack
Crypto exchange BigONE hacked for over $27 million in hot wallet exploit | The Block, accessed July 19, 2025, https://www.theblock.co/post/362814/bigone-hack
BigONE Hack Bounty Program - HackenProof, accessed July 19, 2025, https://hackenproof.com/programs/bigone-hack-bounty-program
The Big One - CFO Leadership, accessed July 19, 2025, https://cfoleadership.com/the-big-one/
The “Big One” Just Hit: The U.S. Cyber Attack Discovered in December 2020 - Withum, accessed July 19, 2025, https://www.withum.com/resources/the-big-one-just-hit-the-us-cyber-attack-discovered-in-december-2020/
BigONE Exchange Suffers Supply Chain Attack, Losses Exceed $27 M - Crypto News, accessed July 19, 2025, https://cryptonews.com/news/bigone-exchange-suffers-supply-chain-attack-losses-exceed-27m/
BigONE - Rekt, accessed July 19, 2025, https://rekt.news/bigone-rekt
What Can We Learn from the BigONE Incident? - OneSafe Blog, accessed July 19, 2025, https://www.onesafe.io/blog/bigone-breach-crypto-security-lessons
Hackers Steal $27 Million from BigONE Exchange in Supply Chain Attack - CoinCentral, accessed July 19, 2025, https://coincentral.com/hackers-steal-27-million-from-bigone-exchange-in-supply-chain-attack/
Hacker steals $27 million in BigONE exchange crypto breach - Bleeping Computer, accessed July 19, 2025, https://www.bleepingcomputer.com/news/security/hacker-steals-27-million-in-bigone-exchange-crypto-breach/
Crypto Bug Bounty Programs 2025 - HackenProof, accessed July 19, 2025, https://hackenproof.com/programs
BigONE Global Exchange: Program Info - HackenProof, accessed July 19, 2025, https://hackenproof.com/programs/bigone-global-exchange
Crypto Hacked or Stolen? Lawyer's 15 Steps to Recovery - Dilendorf Law Firm, accessed July 19, 2025, https://dilendorf.com/resources/crypto-stolen-15-steps-to-take-after-a-cryptocurrency-account-hack-attorney.html
Crypto-Asset Recovery: Challenges, Observed Practices and Strategies - RUSI, accessed July 19, 2025, https://static.rusi.org/special-resource-crypto-asset-recovery-challenges-final.pdf
Bounties Playing Prominent Role in Stolen Cryptocurrency Recovery Efforts | TRM Insights, accessed July 19, 2025, https://www.trmlabs.com/post/bounties-playing-prominent-role-in-stolen-cryptocurrency-recovery-efforts
Can cryptocurrency platforms claim paying attackers is a “White Hat Bounty”? - Red Goat, accessed July 19, 2025, https://red-goat.com/can-cryptocurrency-platforms-claim-paying-attackers-is-a-white-hat-bounty/
Rebuilding Trust in Cryptocurrency Exchanges after Cyber-attacks - ScholarSpace, accessed July 19, 2025, https://scholarspace.manoa.hawaii.edu/bitstreams/47ac9f43-9543-4748-95e1-2adb25e59b52/download
The importance of bug bounty programs in cybersecurity - Block&Capital, accessed July 19, 2025, https://blockandcapital.com/en/bug-bounty-programs/
Lazarus Group Pulled Off 2020's Biggest Exchange Hack and Appears to be Exploring New Money Laundering Options - Chainalysis, accessed July 19, 2025, https://www.chainalysis.com/blog/lazarus-group-kucoin-exchange-hack/
KuCoin has recovered 84% of affected funds in $280M hack, co-founder says | The Block, accessed July 19, 2025, https://www.theblock.co/linked/84248/kucoin-280m-stolen-recovered
KuCoin CEO says 84% of stolen cryptocurrency has been recovered | Cyware Alerts, accessed July 19, 2025, https://www.cyware.com/news/kucoin-ceo-says-84-of-stolen-cryptocurrency-has-been-recovered-40b553df
Binance - Wikipedia, accessed July 19, 2025, https://en.wikipedia.org/wiki/Binance
Binance disaster recovery efforts praised following $40m crypto-hack | The Daily Swig, accessed July 19, 2025, https://portswigger.net/daily-swig/binance-disaster-recovery-efforts-praised-following-40m-crypto-hack
$570M Binance Hack: What Happened & Who Is Responsible? - PurpleSec, accessed July 19, 2025, https://purplesec.us/breach-report/binance-coin-hack/
Binance Hacking Lawsuit | Levin Law, P.A., accessed July 19, 2025, https://www.levinlawpa.com/cryptocurrency-hacking-fraud-lawsuits/binance-hacking-lawsuit/
Bounty Systems: Can They Keep Us Safe? - OneSafe Blog, accessed July 19, 2025, https://www.onesafe.io/blog/bounty-systems-crypto-security
Hacker Returns 90% of Stolen Funds to Texture Protocol - AInvest, accessed July 19, 2025, https://www.ainvest.com/news/hacker-returns-90-stolen-funds-texture-protocol-2507/
Bybit offers 10% bounty to anyone who assists in recovering funds from $1.4 billion hack, accessed July 19, 2025, https://www.theblock.co/post/342830/bybit-offers-10-bounty-to-anyone-who-assists-in-recovering-funds-from-1-4-billion-hack
Crypto Bug Bounties: How to Get Started - Coinmetro, accessed July 19, 2025, https://www.coinmetro.com/learning-lab/crypto-bug-bounties-how-to-get-started
What is What is a bug bounty in crypto & cybersecurity & how it works - CoinTracker, accessed July 19, 2025, https://www.cointracker.io/learn/bug-bounty
A Survey of Bug Bounty Programs in Strengthening Cybersecurity and Privacy in the Blockchain Industry - MDPI, accessed July 19, 2025, https://www.mdpi.com/2813-5288/2/3/10
Hackers Drain $27M From BigONE Exchange, Onchain Sleuth Says “I do not feel bad”, accessed July 19, 2025, https://www.blocmates.com/news-posts/hackers-drain-27m-from-bigone-exchange-onchain-sleuths-say-no-sympathy
Crypto exchange BigONE hacked for over $27 million in hot wallet exploit - Reddit, accessed July 19, 2025, https://www.reddit.com/r/CryptoCurrency/comments/1m16nbj/crypto_exchange_bigone_hacked_for_over_27_million/
BigONE Exchange Loses $27 Million in Supply Chain Cyberattack - Brave New Coin, accessed July 19, 2025, https://bravenewcoin.com/insights/bigone-exchange-loses-27-million-in-supply-chain-cyberattack
The BigONE Exchange 2023 Review: Features, and FAQs - ZenLedger, accessed July 19, 2025, https://zenledger.io/exchanges/bigone/
Crypto.com | Bug Bounty Program Policy - HackerOne, accessed July 19, 2025, https://hackerone.com/crypto
Do you know any good bug bounty program? : r/bugbounty - Reddit, accessed July 19, 2025, https://www.reddit.com/r/bugbounty/comments/1khpfhf/do_you_know_any_good_bug_bounty_program/
I think a company in hacker one kind of tricked me. : r/bugbounty - Reddit, accessed July 19, 2025, https://www.reddit.com/r/bugbounty/comments/1ko0cxz/i_think_a_company_in_hacker_one_kind_of_tricked_me/
Preventing Large-Scale Crypto Hacks: Key Security Measures for Exchanges - Chainalysis, accessed July 19, 2025, https://www.chainalysis.com/blog/preventing-crypto-hacks-best-practices-for-exchanges-hexagate/
Crypto Exchange Hacks: Lessons Learned from Major Security Breaches - OSL, accessed July 19, 2025, https://www.osl.com/hk-en/academy/article/crypto-exchange-hacks-lessons-learned-from-major-security-breaches
Crypto Recovery Group: Overview of Cryptocurrency Recovery & Fraud | Go Legal, accessed July 19, 2025, https://go-legal.co.uk/wp-content/uploads/2023/10/Crypto-Recovery-Group-Overview-of-Cryptocurrency-Recovery-and-Fraud.pdf
Investigation on fake trade volume of top crypto exchanges: BigONE | by Hacken.AI, accessed July 19, 2025, https://hackenclub.medium.com/investigation-on-fake-trade-volume-of-top-crypto-exchanges-bigone-8ba26eff563a
Trust Score Explained - CoinGecko Blog, accessed July 19, 2025, https://blog.coingecko.com/trust-score-explained/
Is BigONE safe? BigONE exchange safety ranking | CER.live, accessed July 19, 2025, https://cer.live/exchange/bigone
KuCoin vs. Binance - Weirdo.Rocks, accessed July 19, 2025, https://www.weirdo.rocks/reviews/kucoin-vs-binance
Crypto.com Launches Massive $2m Bug Bounty Program - Infosecurity Magazine, accessed July 19, 2025, https://www.infosecurity-magazine.com/news/cryptocom-launches-2m-bug-bounty/